You will learn how to:
- Use Kobble to generate Supabase JWT tokens
- Configure your RLS policies based on your Kobble Users IDs
- Use the Supabase client with Kobble to access your Supabase database from your frontend
Pre-requisites: You need to set up your Kobble account before starting this guide.
Getting started
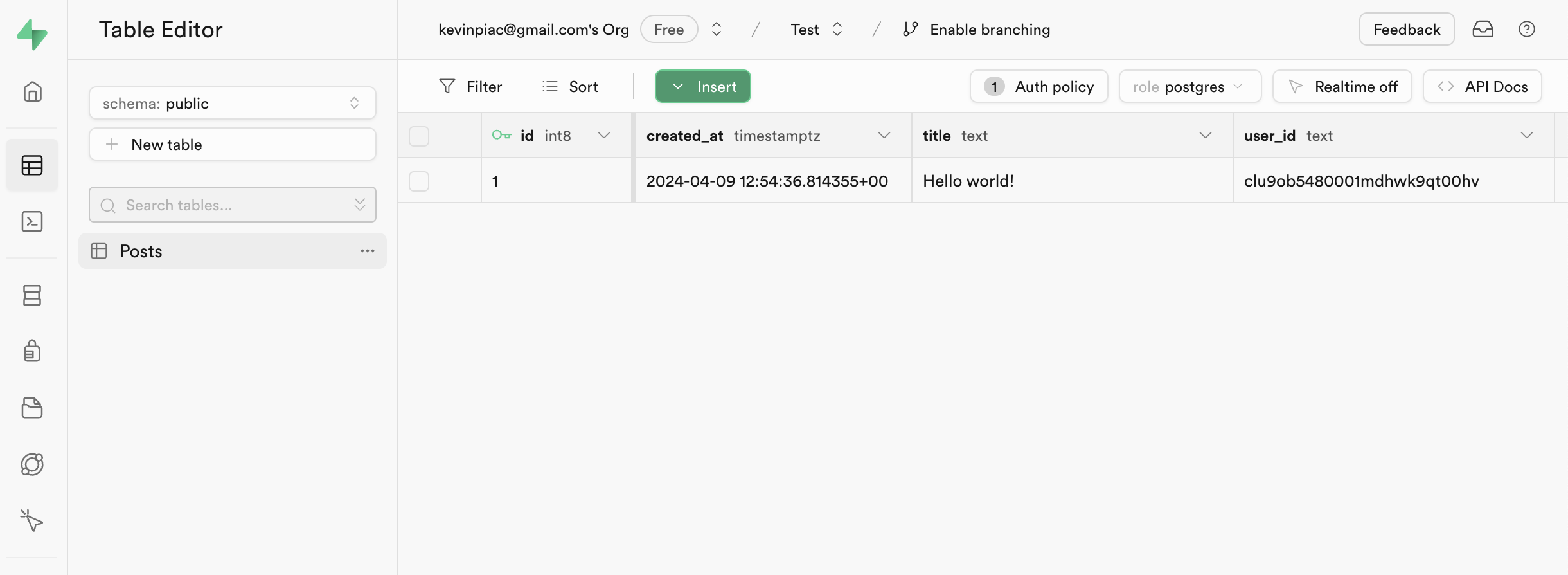
Here’s a diagram illustrating how Kobble and Supabase work together in this tutorial.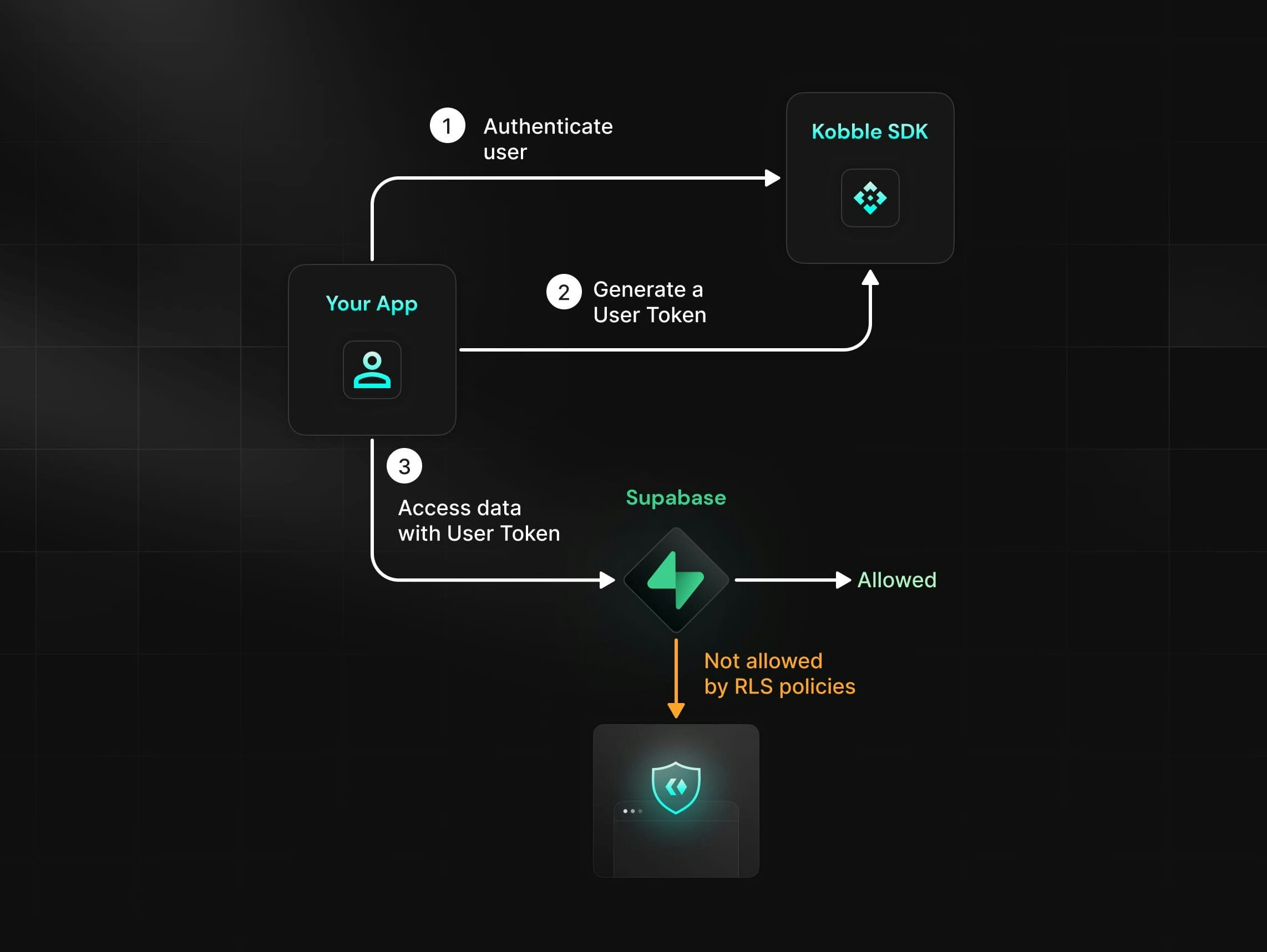
Create a SQL query that checks the user ID
Create a function named
request_user_id(), which will get the Kobble user ID of the requesting user from the request headers.This will allow you to access the user ID in your RLS policies that we’ll configure later.- In the sidebar of your Supabase dashboard, navigate to SQL Editor.
- Select New query.
- Paste the following into the editor:
- Select Run to execute the query and create our function.
Add a column for user IDs to your Supabase tables
To allow users access to their own data, you need to create a RLS policy that uses the User ID sent in the request.By storing the User ID in your tables, you can use it in your RLS policies to compare the requester’s ID with the User ID in the table.In this tutorial, we’ll add a 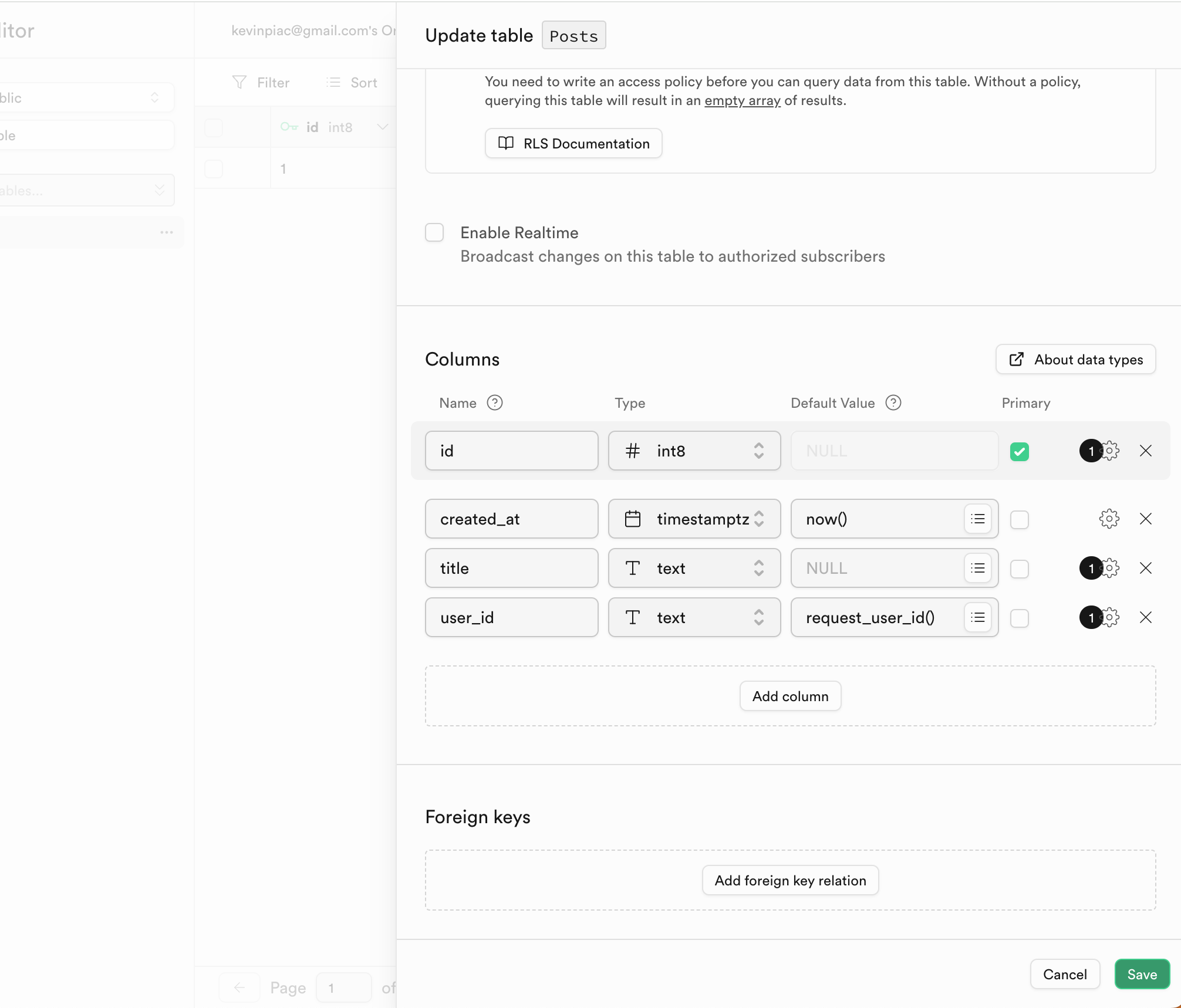
user_id column to a Posts table as an example.So we’ll assume that you have a Posts table in your Supabase database and we want only Post owners to be able to create, update, and view their own posts.- In your Supabase dashboard, navigate to Database > Tables.
- Select the table you want to add the
user_idcolumn to. - Click on Insert a column and fill in the following details:
- Name:
user_id - Type:
text - Default:
(request_user_id()). This will make it default to the return value of the custom function we’ve defined earlier. Doing this user’s ID will be available to Supabase from the request headers.
- Name:

Create RLS policies based on the User ID
For our example, we want to allow users to create, update, and view their own posts only.In your Supabase dashboard, navigate to Authentication > Policies.
Under the name of the table you want users to have access to, select New Policy.Open the SQL Editor and paste the following code:We can repeat the same operation as you did for the
INSERT policy but for to allow UPDATE and SELECT operations:Note that this is only an example for this tutorial. You can create more complex policies based on your needs.
Get your Supabase JWT secret key
To give users access to your data, Supabase’s API requires an authentication token.The Kobble SDK will generate this authentication token for you, but it needs your Supabase project’s JWT secret key first.
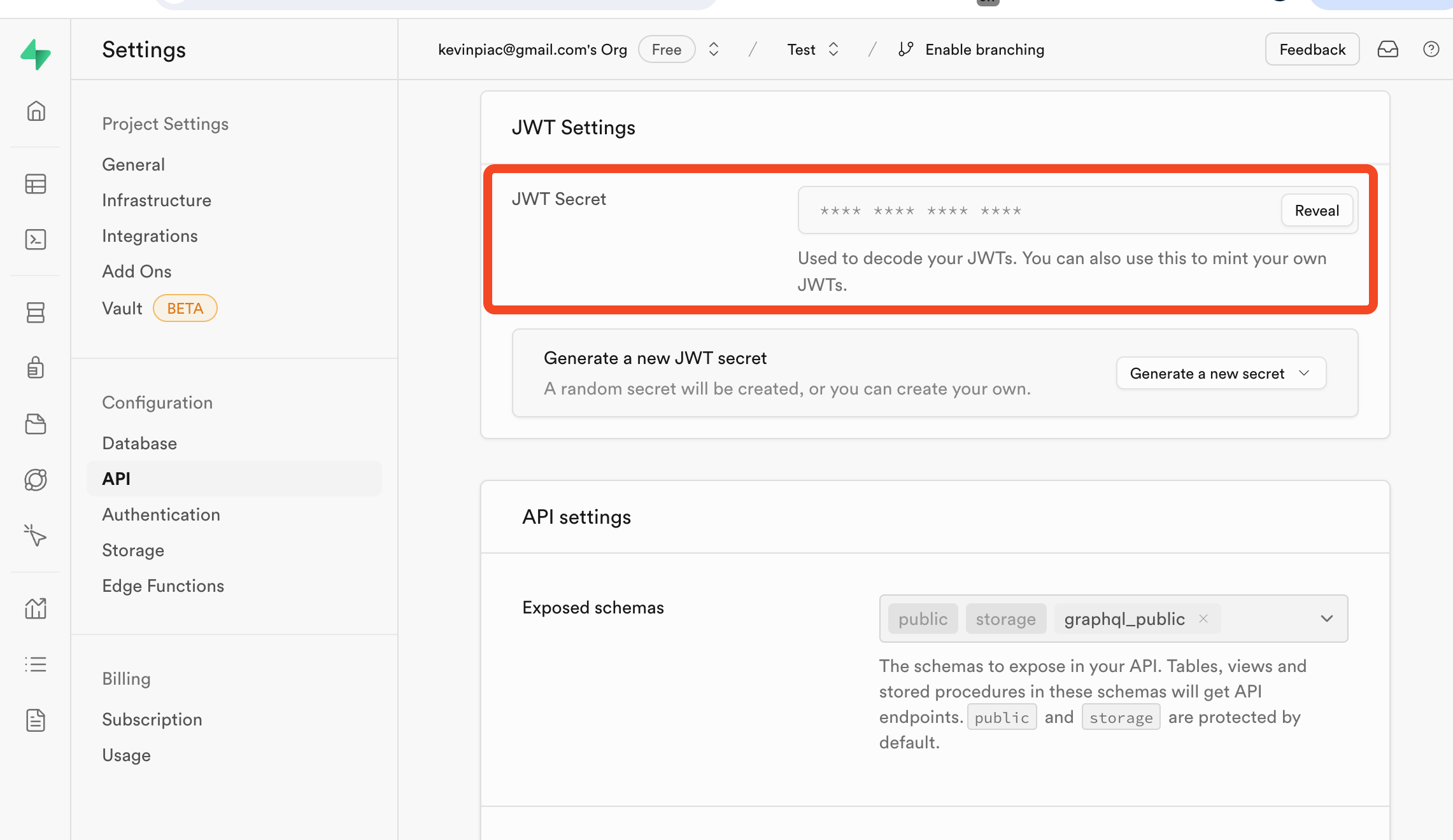
- Find the JWT secret key in your Supabase dashboard:
- In your Supabase dashboard, select Project Settings > API.
-
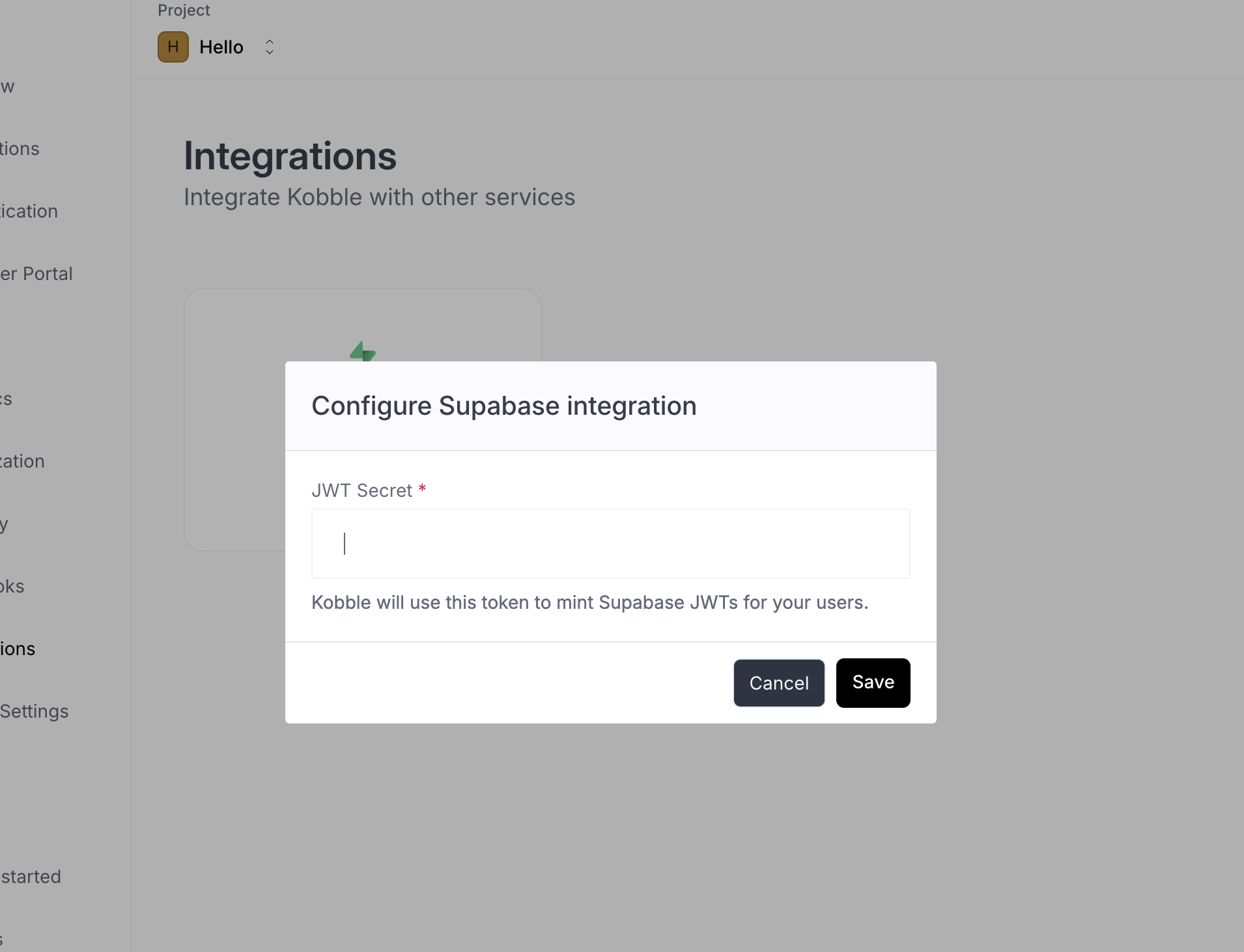
Copy the value in the JWT Secret field.
- Paste it on Kobble
- Open your Kobble dashboard and go to Integrations.
- Click on the Supabase integration.
-
Paste the JWT secret key in the field provided.
Setup your supabase client
- Install the Supabase client and kobble sdk in your project.
Here we’re using the @kobbleio/javascript package, which is the Kobble SDK for Single Page Applications. But you can check our quickstart guides for more examples.
- Initialize your Kobble SDK (either React SDK, Vanilla SDK, or Vue SDK) with as shown in our quickstart guides.
- Export a new Supabase client instance which will use the Kobble token.
Use the Supabase client in your app
Now you can use the supabaseClient anywhere in your app.Here’s an example function that will save a Post to your Supabase database:Here, the supabase client will automatically send the Supabase JWT generated by Kobble to Supabase.
Supabase will accept the request due to our RLS policies that check the user ID in the request headers.